In cybersecurity, we love giving silly names to cyber attacks... phishing, smishing, vishing, and what the heck is quishing? Some people think they are clever, I guess. ClickFix is no different.
We use these same silly names (in most cases) to keep our readers and clients aligned with the terms in general use. At least in this case, the name represents most of the attack tactics.
We've been battling these types of attacks for years with annoying and sometimes malicious pop-ups in Google Chrome. A drive by extension is installed, a notification enabled, a malicious ad makes it past the reviewers. All of these will likely lead to a scare tactic pop up in your browser telling you to patch or that your computer has been seized by some scary law enforcement organization. This one is a next step in that direction and has taken off with attackers. We've reported on it before, but it's more than a flash in the pan as are so many other attacks.
These "ClickFix" attacks are typically the ones that require a little more work from you than just a click and are styled as you "fixing" a problem. To be truly effective (for the attacker, anyway), the attacks needs you to paste and run some code in the computer yourself, conveniently bypassing several layers of security.
The attack will ask you to hit the Windows and R keys (to open the Run dialog), hit the Ctrl-V keys to paste the code that they've conveniently copied to the clipboard for you, and then click run. Pro Tip: never do this.
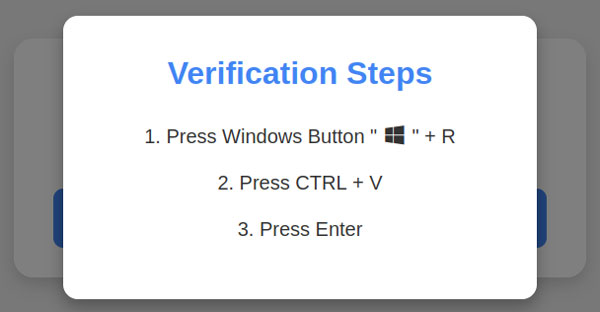
Attackers are finding it harder and harder to get around our protective measures so they are doing more to enlist you, as the user, in their nasty campaigns. Browsers and other tools will "sandbox" code to varying extents protecting you from some mistakes, but Windows-R is like giving attackers the keys to your house, closing your eyes, and sticking your fingers in your ears.
In short, if someone or some piece of software is asking you to hit the Windows-R keys, you should be immediately wary. Make the attacker work for their breach, don't just hand it to them.


