One constant in the universe is that cyber attackers, phishers, and scammers will always have creative new ways to separate you from your money and sensitive information. That is certainly true of this "prove you are human" scam.
The "prove you are human" functionality has been around since computers became connected enough where attackers were able to automate attacks. If you have a website with a "Contact Us" functionality you may also know how much spammers like to automate sending their garbage messages to the masses.
These CAPTCHA tests were invented in the late 1990s and became popular in the early 2000s as a way to separate human from machine when acting on user input. If the user couldn't pass the CAPTCHA, the input could be thrown out as fraudulent. This was used in forum post submissions, online classified ad pages, blogs, site logins, and more. You saw it everywhere at one point. You may have noticed it less in recent times, though. That's because Computer Scientists have devised less obtrusive ways to make this determination. You may have even noticed a little CAPTCHA box that seems to check itself.
Even though CAPTCHA and "prove you are human" are happening more in the background and don't require human interaction as much, our scammers have made their fraudulent version more complex, not less.
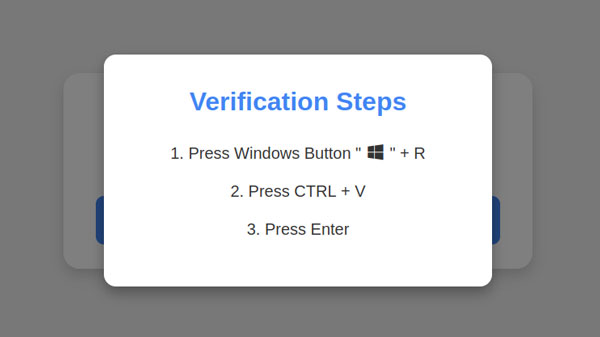
In this attack, the attacker copies malicious code into your clipboard for you (so nice of them). The pop-up then instructs you to press a key combination that allow you to run code on your local machine (Windows-R). The next steps instruct you to past that code (Control-V) and press Enter, thereby running the code.
What an ingenious way to get around having to smuggle that malicious code past your email virus scanner, your computer's anti-virus, and any protections in your browser. At this point, you can only hope that your security monitoring tools detect and/or block the suspicious activity. You should never copy and paste code from an email or the web into your computer's run functionality, command prompt, PowerShell terminal, or anything else similar.
This is another great example where user education trumps a tech-only security cybersecurity solution. Even with all the tools we have at our disposal, the attackers will be one step ahead. You decrease that advantage by educating your users to spot anything unusual and better understand the motivations of the attackers.