Three recently discovered attacks have me a bit more worried than usual. The technical attacks against infrastructure are typically pretty easy to patch up and prevent (as long as the vendors do their part!). It's the social engineering attacks that worry me the most.
We can't install AV, EDR, XDR, MDR, Firewalls, IDS/IPS, etc., in the human brain so we have to rely on training for the most part. We do have some tools that filter emails but those don't extend to phone calls and text messages and they aren't a 100% perfect solution. This is why attackers lean on social engineering and phishing so heavily.
Three recent attacks seem to play on a lack of tech savviness among many computer users today. Of course, we've given a few of these silly names: ClickFix and FileFix. The names are pretty dumb, as usual, and don't reflect the nature of the attack well. However, that's what the industry is using so we must, as well. The third attack uses App Passwords and is, so far, limited to nation state attackers but we'll dig into that more later.
First, ClickFix and FileFix are similar enough to group together. We've actually reported on ClickFix in the past but wanted to link the two attacks here for better understanding. They both abuse the user's lack of tech knowledge to get them to copy and paste malicious code into places that their computer can execute commands. ClickFix has the user copy and paste into the Run dialog and FileFix has them copy and paste into File Explorer. The attacker takes advantage of the small space in both of these spots to hide the malicious code and only show the user something benign.
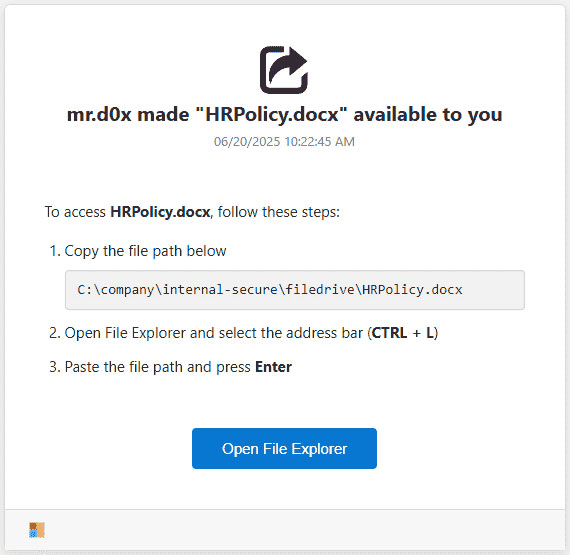
In this case, the user sees a file path which looks pretty benign but doesn't see malicious code above it in the specifically crafted text box.
We expect to see more of these type attacks as attackers discover other ways to execute code on systems. We may see some where users are asked to copy and paste into Excel or Chrome. Both have the ability to affect the system in ways that may be advantageous to cyber criminals. Be wary anytime you are asked to copy and paste code from a website or email into any functionality on your system!
The other attack is focused more on cloud services and has, thus far, only been spotted being used by nation state attackers. We don't expect that barrier to hold, though. Copycats are quick to jump on these low cost, novel means of getting access to accounts and sensitive information.
The attack involves App Passwords which are a way to continue allowing older applications to access online accounts without hooking into the new authentication protocols (read: MFA). Attackers are taking advantage of most user's lack of knowledge of app passwords. The Russian attackers have built some very official looking guidance on granting access for, what appears to be, legitimate use cases. Perhaps the copycat attackers will do the same or they may just phone it in hoping to net the lowest hanging fruit. Either way, be mindful of this attack while you are in your inbox.
The bottom line for all of these attacks is: Be careful when being asked to do technical things that are outside of your knowledge. For our clients, we are always here to help you with those technical requests. If you suspect phishing in email, click that Ironscales Report Phishing button. If it's a suspicious call or text message, give us a call or submit a ticket.
References:
https://krebsonsecurity.com/2025/03/clickfix-how-to-infect-your-pc-in-three-easy-steps/
https://thehackernews.com/2025/06/new-filefix-method-emerges-as-threat.html
https://thehackernews.com/2025/06/russian-apt29-exploits-gmail-app.html


