By now, you've probably seen the unpaid toll text message phish about 100 times or more. I know we've been talking about it quite a bit lately.
We aren't necessarily amazed by the theme in this one, but more leery of a tactic employed to get your help in phishing you. In "the more you know" fashion, knowing this could help you understand and prevent many more text phishing scams.
If you received one of these text phishing messages, you certainly saw the "answer yes" part at the bottom.
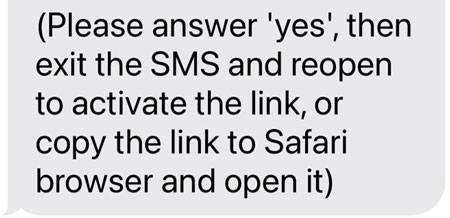
As with our warning about running code on your PC last month, attackers are finding it harder and harder to get around our protective measures so they are doing more to enlist you, as the user, in their nasty campaigns. So how are they doing that here?
If you are an iPhone user, Apple does not activate any links in the initial message of a conversation. It errs on the side of caution as those first messages may be unsolicited and dangerous. However, when you interact with the sender, Apple assumes the message is legitimate and will enable the tappable link the next time. you open the message. You interact by responding to a message, hence the "answer yes" directive.
Attackers are banking that you don't know this and want you to help in bypassing this safeguard.
While we are mostly seeing this in the unpaid toll scam, it's starting to show up in other themes as well. I expect this to be used by the attackers for a while to come.
If you see something that resembles this paragraph at the end of a text message, you can be 100% certain that it is a phishing attack. You can safely delete and report it knowing you've just prevented yourself a world of hurt.
Watch for variations on the methods to elicit a response, as well. Attackers aren't stupid. They'll shape this tactic over time to get as much out of it as they can. But the general theme of responding to an unsolicited message to activate the link should be the same through all.


